What is phishing? Seven tips to avoid phishing attacks
( 5 min. read )
- Go back to blog home
- Latest
The goal of phishing attacks is to get you to provide sensitive information accidentally, give access to a network, or download malware.

An example of a modern day, sophisticated phishing attack is the use of typo-squatted domain names. While this sounds very technical, it’s actually quite simple. The criminals set up a website pretending to be Adobe, but their web address uses the Latin character “ḅ” instead of the normal “b”, so you got “adoḅe.com” – note the dot under the b.
From there, the attacker can make “adoḅe.com” an HTTPS site and create numerous other sub-sites. Such a site like “get.adoḅe.com” could be created and emailed out to target accounts as a link. And of course, hyperlinks have an underlining which masks the false character, meaning the link looked 100% legitimate. As per the example below, the dot below the “b” cannot be seen because the hyperlink underline has covered it over:
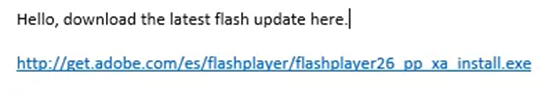
This is just one example, and there are many ways phishing attacks can happen. However, there are practical steps to combat phishing attacks and mitigate the risk:
- Train your employees on how they can identify malicious emails, and know what to do with them. Run simulated phishing campaigns and anti-phishing penetration tests.
- Ensure employees use strong, unique passwords for their work accounts, and communicate that passwords for company accounts should be different from their personal email accounts.
- Use Multi-Factor Authentication (MFA) to reduce the risk of unauthorised account takeovers.
- Educate staff about the risks of social engineering. Encourage them not to post work-related information on public social media platforms that could be used to identify their employer, their position and responsibilities etc, and so be used for a targeted phishing attack.
- Install a secure email gateway with anti-spam, anti-malware, and policy-based filtering. This could also include SPF (Sender Policy Framework), DMARC (Domain-Based Message Authentication, Reporting & Conformance), and DKIM (Domain Keys Identified Mail), as well as anomaly detection for inbound and outbound emails.
- If you have any doubts about an email or have suspects about the links, report it to your Security Team immediately. They can check the email, and get any suspicious links or sites opened in a sandbox environment. They will then tell you if the email is genuine.
- Review mitigation measures and ensure system updates take place periodically.
Phishing can be conducted via email, text message, social media, or by phone. With phishing attacks becoming increasingly sophisticated and challenging to detect, it is crucial to stay vigilant and informed to prevent them. The Ebury team is here to help our customers embrace best practices to protect their sensitive information.
📩 If you need any advice on any fraud-related issues, contact us at [email protected].

